Another day, another opportunity to see what other firewall distros can be deployed on this old Watchguard Firebox x500. In this case I’ll try ZeroShell. I’ve used ZeroShell many times in the past, typically as a small VM. ZeroShell is one of the fastest and easiest Firewall Distros I’ve tried. Back in the day when I was trying to see if I can bond multiple cable modems together for site-to-site connections I’ve used ZeroShell due to it’s very easy bonding of OpenVPN connections.
Another reason why I’m eager to try ZeroShell on this Firebox is the fact that unlike pfSense and m0n0wall, it’s not BSD based OS. It’s actually linux based which means that there’s a very good possibility that the Watchdog Timeout issue might not happen as this seems to be a driver issue in BSD related to the Realtek NICs on the x500.
On to the install process.
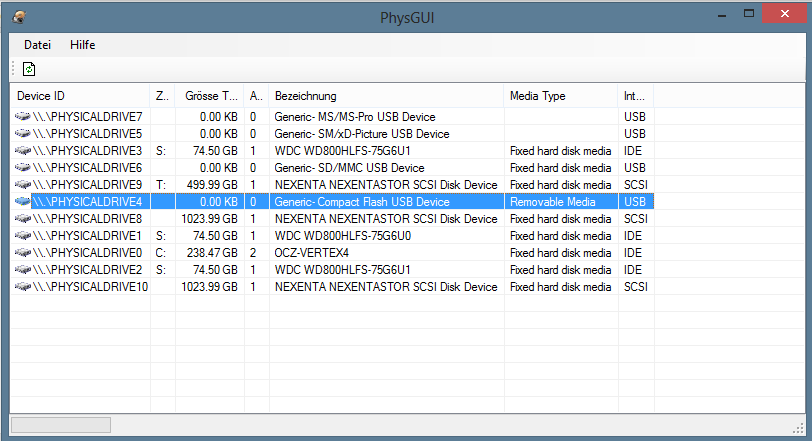
Just like earlier first step is to simply load the firmware image onto the compact flash card. To do that once again need to clean the compact flash card from any existing partitions
Microsoft Windows [Version 6.2.9200]
(c) 2012 Microsoft Corporation. All rights reserved.
C:\Windows\System32>diskpart
Microsoft DiskPart version 6.2.9200
Copyright (C) 1999-2012 Microsoft Corporation.
On computer: ARES
DISKPART> list disk
Disk ### Status Size Free Dyn Gpt
-------- ------------- ------- ------- --- ---
Disk 0 Online 238 GB 0 B
Disk 1 Online 74 GB 0 B *
Disk 2 Online 74 GB 0 B *
Disk 3 Online 74 GB 0 B *
Disk 4 Online 2048 MB 0 B
Disk 5 Offline 1024 GB 0 B *
Disk 6 Online 500 GB 1024 KB *
Disk 7 Online 1024 GB 0 B *
DISKPART> select disk 4
Disk 4 is now the selected disk.
DISKPART> clean
DiskPart succeeded in cleaning the disk.
DISKPART> exit
Leaving DiskPart...
C:\Windows\System32>
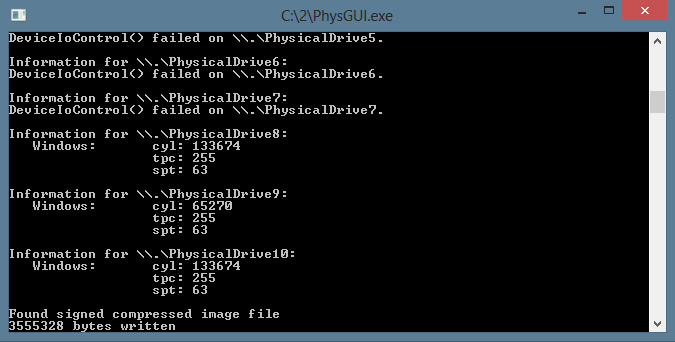
Then use physdiskwrite to write the image onto the card. In this case the image being loaded is the ALIX image that can be downloaded here. The latest image (RC1) requires a minimum 2GB Compact Flash card to write the image to. Luckily I still have a few of those laying around.
Microsoft Windows [Version 6.2.9200]
(c) 2012 Microsoft Corporation. All rights reserved.
c:\2>physdiskwrite.exe ZeroShell-2.0.RC1-Alix-2GB.img
physdiskwrite v0.5.2 by Manuel Kasper
Which disk do you want to write? (0..7) 4
About to overwrite the contents of disk 4 with new data. Proceed? (y/n) y
c:\2>
Once the compact flash card is installed into the firewall, connect the serial cable and use a terminal program at 38400-8-n-1 to watch the bootup process. During my bootup there seemed to be some errors at runtime that actually took a few seconds longer to get going.
ÿ[ 1.004441] platform pc8736x_gpio.0: no device found
[ 31.842568] ata1.00: exception Emask 0x0 SAct 0x0 SErr 0x0 action 0x6 frozen
[ 31.863676] ata1.00: failed command: READ DMA
[ 31.876728] ata1.00: cmd c8/00:08:00:00:00/00:00:00:00:00/e0 tag 0 dma 4096 in
[ 31.876732] res 40/00:00:00:00:00/00:00:00:00:00/00 Emask 0x4 (timeout)
[ 31.920494] ata1.00: status: { DRDY }
[ 62.960333] ata1.00: exception Emask 0x0 SAct 0x0 SErr 0x0 action 0x6 frozen
[ 62.961451] ata1.00: failed command: READ DMA
[ 62.966530] ata1.00: cmd c8/00:08:00:00:00/00:00:00:00:00/e0 tag 0 dma 4096 in
[ 62.966534] res 40/00:00:00:00:00/00:00:00:00:00/00 Emask 0x4 (timeout)
[ 62.970295] ata1.00: status: { DRDY }
[ 94.002083] ata1.00: exception Emask 0x0 SAct 0x0 SErr 0x0 action 0x6 frozen
[ 94.003202] ata1.00: failed command: READ DMA
[ 94.008282] ata1.00: cmd c8/00:08:00:00:00/00:00:00:00:00/e0 tag 0 dma 4096 in
[ 94.008285] res 40/00:00:00:00:00/00:00:00:00:00/00 Emask 0x4 (timeout)
[ 94.012049] ata1.00: status: { DRDY }
Loading Zeroshell ZS-2.0.RC1 ...
DEVICE=/dev/sda2
Mounting ISO image ...
mount: warning: /cdrom seems to be mounted read-only.
Loading root filesystem into RAM device... Success
mount: warning: /.root/cdrom seems to be mounted read-only.
Successfully mounted device ISO
INIT: version 2.85 booting
INIT: Entering runlevel: 3nterface...
[ OK ] udevd daemon...
[ OK ]ing for attached devices...
Checking for other PCI hardware ...
Loading ................................... [pata_acpi]
Loading ................................... [intel-rng]
Scanning for SCSI,SATA,IDE,USB storage devices...
--------------------------------------------------------------------
PROFILE : Default Profile
Disk : ATA SanDiskSDCFH-20
Partition : sda3
Alias : _DB.001
--------------------------------------------------------------------
[ OK ]Time Zone [Europe/Rome]
[ OK ] Clock (LOCALTIME) --> System Time
[ OK ]hostname to zeroshell.example.com
[ OK ] configuration files...
[ OK ]ng swap file...
Starting X.509 Certification Authority...
Generating zeroshell.example.com host certificate ...
Generating a 2048 bit RSA private key
...........................................+++
............+++
writing new private key to '/tmp/x509default.key'
-----
Using configuration from /etc/ssl/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 3 (0x3)
Validity
Not Before: Nov 9 22:43:38 2012 GMT
Not After : Nov 9 22:43:38 2014 GMT
Subject:
organizationalUnitName = Hosts
commonName = zeroshell.example.com
X509v3 extensions:
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Subject Alternative Name:
DNS:zeroshell.example.com, IP Address:192.168.250.254, IP Address:192.168.0.75
Certificate is to be certified until Nov 9 22:43:38 2014 GMT (730 days)
Write out database with 1 new entries
Data Base Updated
Generating admin user certificate ...
Generating a 2048 bit RSA private key
.........................................................+++
....+++
writing new private key to '/tmp/x509default.key'
-----
Using configuration from /etc/ssl/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4 (0x4)
Validity
Not Before: Nov 9 22:43:40 2012 GMT
Not After : Nov 9 22:43:40 2014 GMT
Subject:
organizationalUnitName = users
commonName = admin
X509v3 extensions:
X509v3 Key Usage:
Digital Signature, Key Encipherment, Data Encipherment
X509v3 Extended Key Usage:
TLS Web Client Authentication, E-mail Protection
Certificate is to be certified until Nov 9 22:43:40 2014 GMT (730 days)
Write out database with 1 new entries
[ OK ]e Updated
[ OK ] LDAP daemon...
[ OK ] DNS service...
[ OK ] system log daemon...
[ OK ] kernel log daemon...
[ OK ]connection tracking modules (h323,ftp,sip,irc,pptp,tftp)
[ OK ]NAT tracking modules (ftp,pptp)
[ OK ]g Layer 7 protocol definitions (l7-protocols-2009-05-28)
Starting Firewall...
Starting Captive Portal ...
--> Gateway disabled
--> Web Login Authentication Server disabled
Starting Network...
Starting WiFi subsystem ...
--> No supported Wi-Fi hardware has been found.
Detecting ethernet interfaces...
ETH00 (hardware changed) : Realtek Semiconductor Co., Ltd. RTL-8139/8139C/8139C+ (rev 20)
ETH01 (hardware changed) : Realtek Semiconductor Co., Ltd. RTL-8139/8139C/8139C+ (rev 20)
ETH02 (new) : Realtek Semiconductor Co., Ltd. RTL-8139/8139C/8139C+ (rev 20)
ETH03 (new) : Realtek Semiconductor Co., Ltd. RTL-8139/8139C/8139C+ (rev 20)
ETH04 (new) : Realtek Semiconductor Co., Ltd. RTL-8139/8139C/8139C+ (rev 20)
ETH05 (new) : Realtek Semiconductor Co., Ltd. RTL-8139/8139C/8139C+ (rev 20)
Configuring interfaces...
ETH00: 192.168.0.75/255.255.255.0
VPN99: 192.168.250.254/255.255.255.0
Starting Routing...
Starting Quality of Service on:
NONE. No interfaces configured for QoS
[ OK ] NTP daemon...
[ OK ] Dynamic DNS client daemon...
[ OK ] Log Watcher...
Starting Kerberos 5 KDC
[ OK ]istribution Center process
[ OK ]n administration process
[ OK ] httpd daemon...
Checking HTTP Transparent Proxy and AntiVirus configuration...
[ OK ] cron daemon ...
Starting MRTG ...
[ OK ]ing MRTG ...
[ OK ] Daemon Watcher ...
[ OK ] AutoUpdate daemon...
Zeroshell
[ OK ] caching background process ...
-------------------------------------------------------------------------------
Z e r o S h e l l - Net Services 2.0.RC1 November 09, 2012 - 23:43
-------------------------------------------------------------------------------
Hostname : zeroshell.example.com
CPU (1) : Intel(R) Celeron(TM) CPU 1200MHz 1202MHz
Kernel : 3.4.6-ZS
Memory : 512388 kB http://192.168.0.75
Uptime : 0 days, 0:2 User : admin
Load : 2.12 0.89 0.33 Password : zeroshell
Profile : Default Profile
-------------------------------------------------------------------------------
COMMAND MENU
Activate Profile Change admin password
Deactivate Profile Show Routing Table
Shell Prompt Show Firewall Rules
Reboot Show Network Interface
Shutdown Fail-Safe Mode
Create a Bridge IP Manager
WiFi Manager
Select:
Now that the firewall is up. I configured the WAN and LAN interfaces via the shell. By default the DHCP server on LAN side is not enabled so in order to access the firewall via the browser I had to set a static IP address on my machine. Once the IP has been configured, just launch a the browser and point to the address as displayed in the console (default http://192.168.0.75)
I also disovered that by default the WAN interface allows access to the ZeroShell interface also, and since the firewall WAN is actually on my LAN, I was able to access and configure the UI from my workstation. This also means that it’s very important to change the default password if the firewall is internet facing as anyone coming across it can reconfigure it.
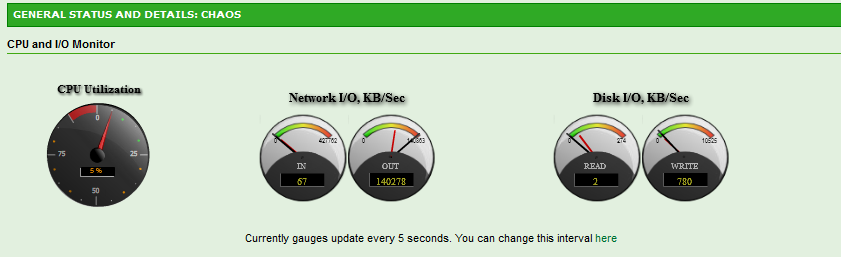
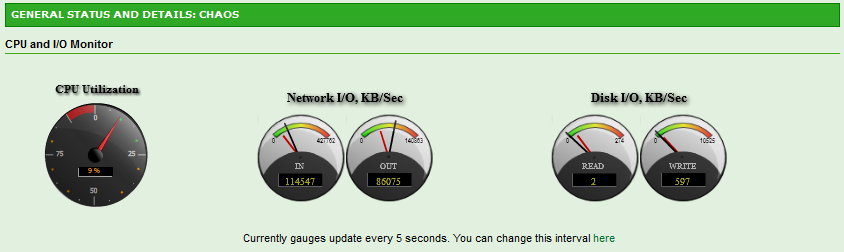
Running some unencrypted performance tests. I was able to achieve 11.9MB/s (95.2 Mbit/s) throughput across the firewall. This is actually not bad considering the same test on this box running pfSense the throughput was 11.1MB/s.
I came across an interesting article on the ZeroShell forums about the HTTP Anti-Virus Proxy and Compact Flash cards. Specifically about the HAVP’s work directory being used during its operation. To create a RAM drive to store these temporary files instead shut down HAVP and execute these commands from console or through SSH:
root@zeroshell root> cd /Database
root@zeroshell Database> dd if=/dev/zero of=HAVP.ext2 count=100000
100000+0 records in
100000+0 records out
root@zeroshell Database> mkfs.ext2 HAVP.ext2
mke2fs 1.42 (29-Nov-2011)
HAVP.ext2 is not a block special device.
Proceed anyway? (y,n) y
Discarding device blocks: done
Filesystem label=
OS type: Linux
Block size=1024 (log=0)
Fragment size=1024 (log=0)
Stride=0 blocks, Stripe width=0 blocks
12544 inodes, 50000 blocks
2500 blocks (5.00%) reserved for the super user
First data block=1
Maximum filesystem blocks=51380224
7 block groups
8192 blocks per group, 8192 fragments per group
1792 inodes per group
Superblock backups stored on blocks:
8193, 24577, 40961
Allocating group tables: done
Writing inode tables: done
Writing superblocks and filesystem accounting information: done
root@zeroshell Database> mount -o loop HAVP.ext2 /mnt
root@zeroshell Database> chown havp.havp /mnt
root@zeroshell Database> umount /mnt
root@zeroshell Database> cat /Database/HAVP.ext2 > /dev/ram3
root@zeroshell Database> mount -omand,noatime /dev/ram3 /Database/var/register/system/havp/tmp
root@zeroshell Database>
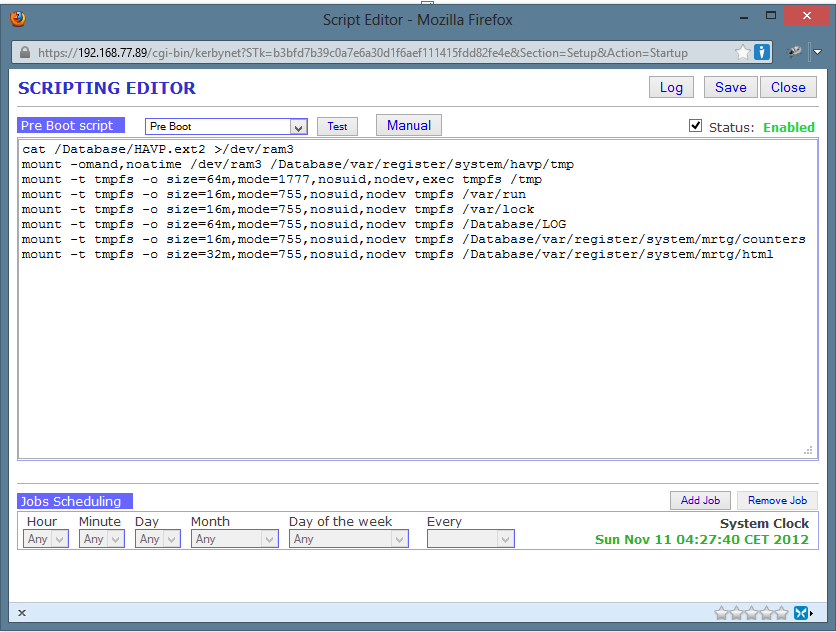
The last two lines have to be added to the pre-boot script so that they execute on device restart.
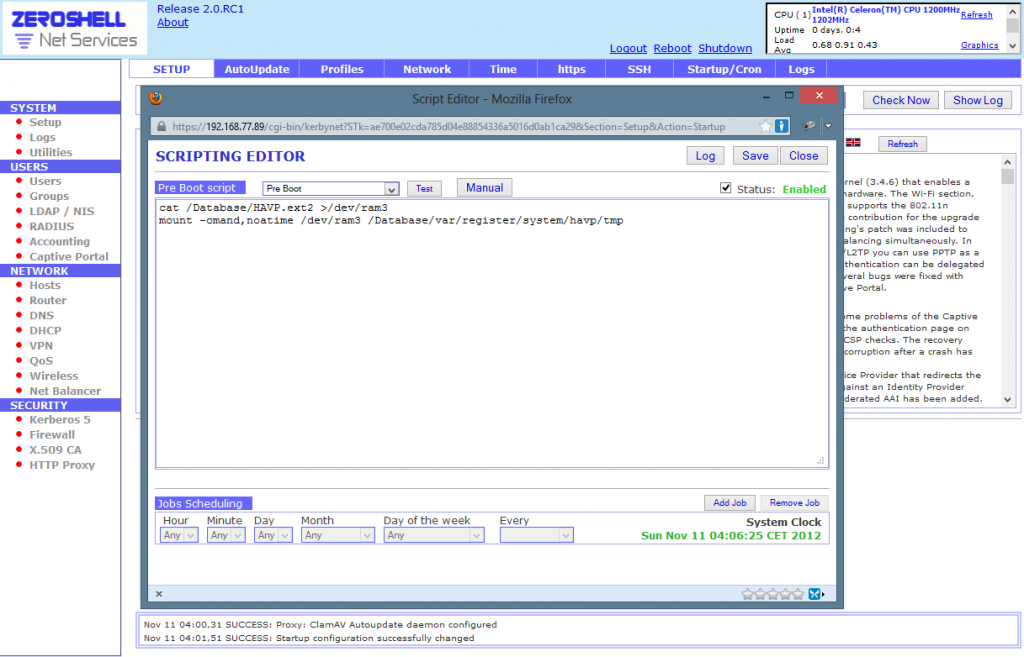
Now just restart the HAVP service and it’s done.
After more than 24 hours of various traffic passing through the firewall, I have not had any issues yet with the Watchguard Timeout. So far so good. The firewall performs pretty well. There’s probably no chance getting the LCD working easily at this point. Though there’s a small possibility that ZeroShell will at one point support LCDProc in which case the LCD can live again.
I have also since added few more remounts to ensure longer CF card life. Apparently just because the ZeroShell distro image is aimed at embedded devices, it still performs regular writes to the local storage. Since CF cards have limited write cycles, remounting the writeable locations in RAM drive should significantly extend the life of the Compact Flash card.
mount -t tmpfs -o size=64m,mode=1777,nosuid,nodev,exec tmpfs /tmp
mount -t tmpfs -o size=16m,mode=755,nosuid,nodev tmpfs /var/run
mount -t tmpfs -o size=16m,mode=755,nosuid,nodev tmpfs /var/lock
mount -t tmpfs -o size=64m,mode=755,nosuid,nodev tmpfs /Database/LOG
mount -t tmpfs -o size=16m,mode=755,nosuid,nodev tmpfs /Database/var/register/system/mrtg/counters
mount -t tmpfs -o size=32m,mode=755,nosuid,nodev tmpfs /Database/var/register/system/mrtg/html